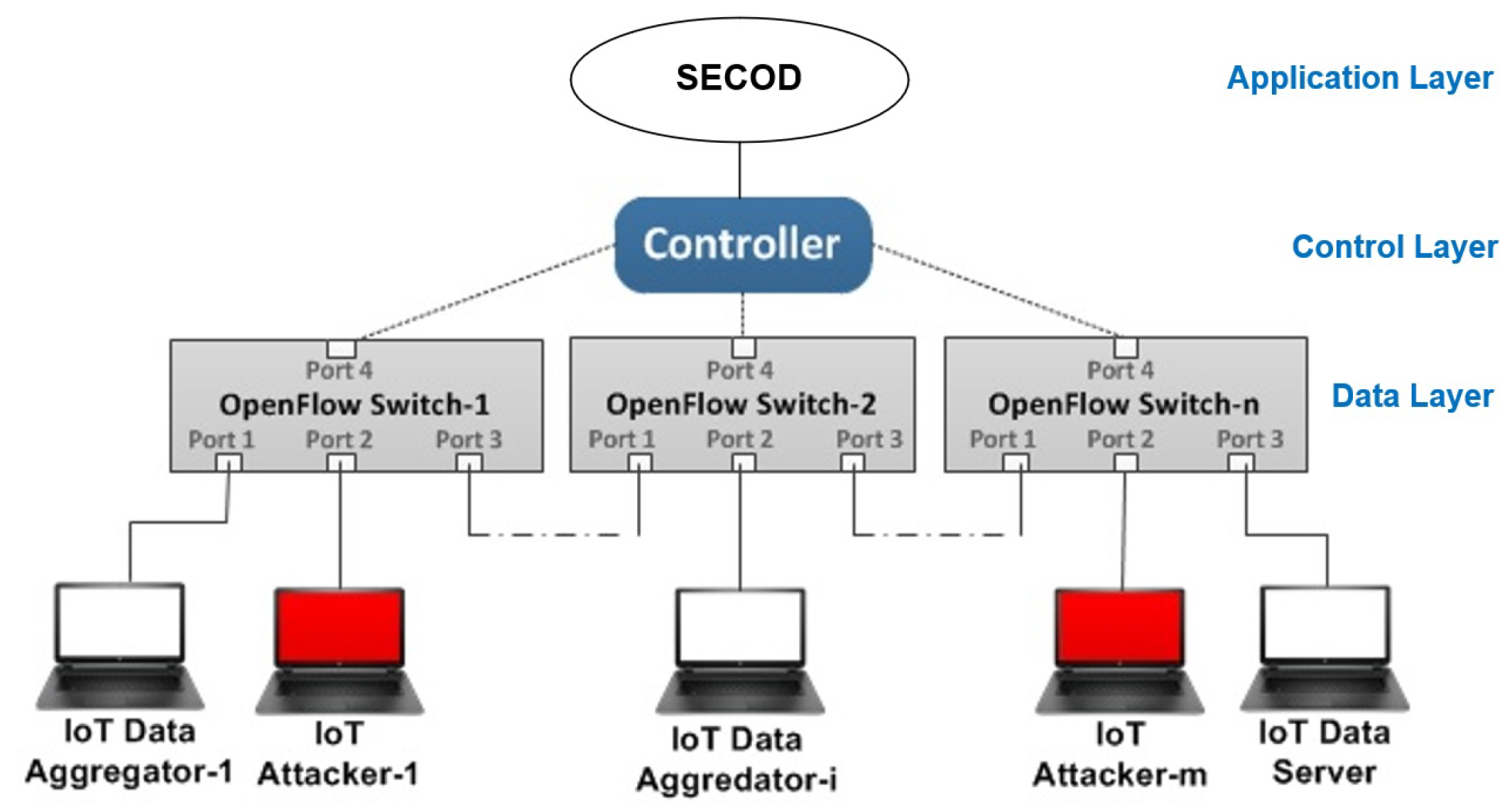
Applied Sciences | Free Full-Text | Mitigating DDoS Attacks in SDN-Based IoT Networks Leveraging Secure Control and Data Plane Algorithm
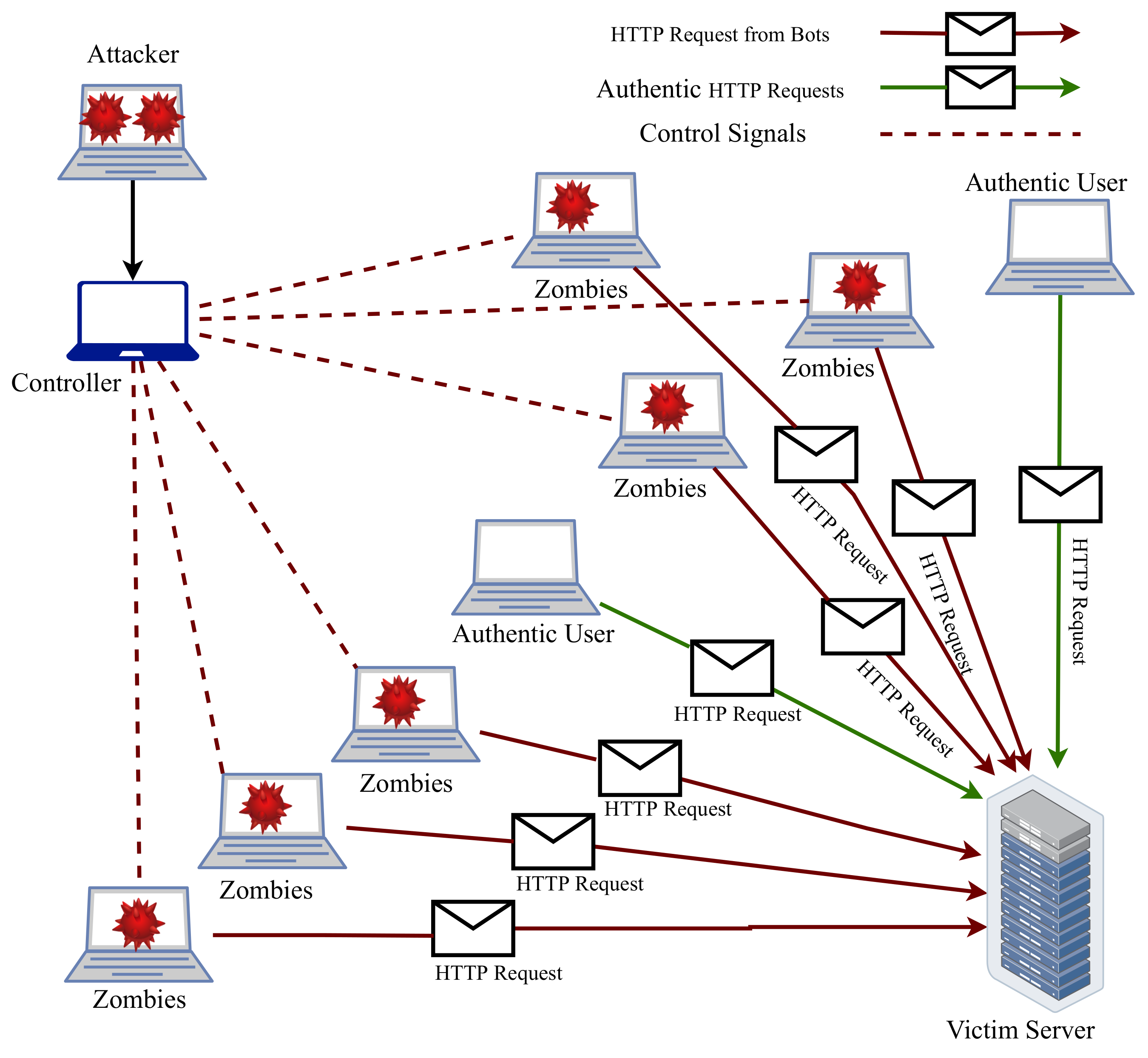
Electronics | Free Full-Text | Denial of Service Attack Classification Using Machine Learning with Multi-Features
Wifi Router Lock Color Icon Vector Illustration Stock Illustration - Illustration of email, ddos: 206757150























